A Comprehensive Guide To The FNV Hash Function: Efficiency And Security In Hashing
A Comprehensive Guide to the FNV Hash Function: Efficiency and Security in Hashing
Related Articles: A Comprehensive Guide to the FNV Hash Function: Efficiency and Security in Hashing
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to A Comprehensive Guide to the FNV Hash Function: Efficiency and Security in Hashing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
A Comprehensive Guide to the FNV Hash Function: Efficiency and Security in Hashing
The world of computing relies heavily on efficient and reliable methods for storing and retrieving data. Hash functions, central to this process, play a crucial role in ensuring data integrity and enabling fast lookups. One such function, known as the Fowler-Noll-Vo (FNV) hash function, stands out for its simplicity, speed, and excellent distribution properties. This article delves into the intricacies of FNV, exploring its mechanics, advantages, and applications, providing a thorough understanding of its significance in various computing domains.
Understanding the Fundamentals of Hashing
Before delving into the specifics of FNV, it’s essential to understand the core concept of hashing. A hash function takes an input, typically a string of characters or a piece of data, and transforms it into a fixed-size output called a hash value or hash code. This output is often a numerical representation of the input, allowing for efficient storage and retrieval.
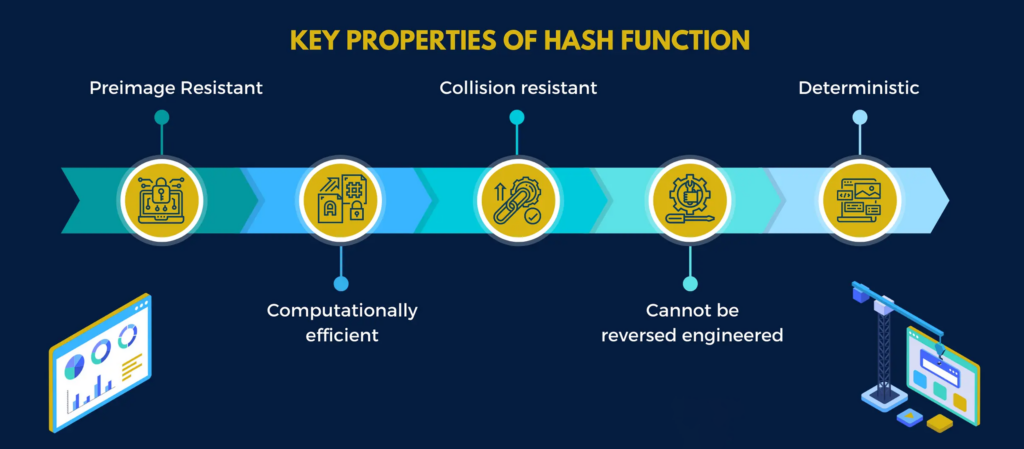
Hash functions are designed to exhibit several key properties:
- Deterministic: Given the same input, the hash function always produces the same output. This ensures consistency and predictability.
- Efficient: The hash function should be computationally inexpensive to compute, allowing for rapid hashing of large datasets.
- Uniform Distribution: Ideally, the hash function should distribute hash values evenly across the output range, minimizing collisions (instances where different inputs produce the same hash value).
The FNV Algorithm: A Detailed Exploration
The FNV hash function, developed by Glenn Fowler, Landon Curt Noll, and Phong Vo, utilizes a simple yet effective algorithm to generate hash values. It operates in two distinct phases:
1. Initialization: The algorithm begins by assigning a specific prime number, referred to as the FNV prime, to a variable called hash. This prime number serves as the initial value for the hash calculation.
2. Iterative Hashing: Each character in the input data is processed sequentially. For every character, the following steps are performed:
-
Multiplication: The current
hashvalue is multiplied by the FNV prime. - XOR Operation: The result of the multiplication is then XORed (exclusive OR) with the ASCII value of the current character.
This iterative process continues until all characters in the input data have been processed. The final value of hash represents the FNV hash value for the input data.
FNV Variants: Tailoring the Hash Function
To cater to diverse requirements, two main FNV variants exist:
- FNV-1a: In this variant, the XOR operation is performed after the multiplication step. This approach is generally preferred for its improved distribution properties.
- FNV-1: Here, the XOR operation is performed before the multiplication step. While less common, FNV-1 can be useful in certain scenarios.
Choosing the Right FNV Prime:
The choice of FNV prime plays a crucial role in the effectiveness of the hash function. Different FNV primes are designed to provide optimal performance and distribution for specific use cases. Common FNV primes include:
- FNV Prime 32: 16777619 (for 32-bit hash values)
- FNV Prime 64: 1099511628211 (for 64-bit hash values)
Benefits of the FNV Hash Function
The FNV hash function offers several advantages that make it a popular choice in various applications:
- Speed: FNV’s simplicity and efficient implementation lead to fast hash calculations, crucial for performance-sensitive applications.
- Low Collision Rate: The FNV algorithm exhibits a low collision rate, meaning that different inputs are less likely to produce the same hash value. This is crucial for maintaining data integrity and avoiding conflicts.
- Versatility: FNV can be used to hash data of various types, including strings, integers, and binary data, making it versatile for different applications.
- Easy Implementation: The FNV algorithm is straightforward to implement, requiring minimal code and readily available in various programming languages.
Applications of FNV Hashing
The FNV hash function finds widespread application in various domains, including:
- Data Structures: FNV is commonly used in hash tables, a fundamental data structure for efficient data storage and retrieval.
- Caching: FNV enables fast lookups in caches, ensuring quick access to frequently accessed data.
- Checksums: FNV can be used to generate checksums for data integrity verification, ensuring that data remains unaltered during transmission or storage.
- Cryptography: While not a cryptographic hash function, FNV can be used in certain cryptographic applications, such as key derivation and password hashing.
FAQs Regarding FNV Hashing
1. Is FNV a Cryptographic Hash Function?
No, FNV is not a cryptographic hash function. While it provides good distribution and collision resistance, it is not designed to withstand deliberate attacks aimed at generating collisions or reverse-engineering the input from the hash value.
2. When Should I Use FNV?
FNV is an excellent choice for general-purpose hashing when speed and low collision rates are paramount. It is particularly well-suited for applications involving large datasets, where fast lookups and data integrity are crucial.
3. How Secure is FNV?
FNV is not considered cryptographically secure. It is vulnerable to attacks that can generate collisions, potentially leading to data manipulation or security breaches.
4. Are There Alternatives to FNV?
Yes, there are other popular hash functions, including MD5, SHA-1, and SHA-256. These cryptographic hash functions are designed to be more secure than FNV, but they are also computationally more expensive.
5. What are the Limitations of FNV?
While FNV is a robust hash function, it has some limitations:
- Not Cryptographically Secure: FNV is not designed for cryptographic applications and can be vulnerable to attacks.
- Limited Output Size: The output size of FNV is fixed, potentially leading to collisions for very large datasets.
Tips for Using FNV Effectively
- Choose the Appropriate FNV Prime: Select the FNV prime that best suits the size of your data and the desired hash value length.
- Consider Collision Handling: Implement strategies to handle collisions, such as chaining or open addressing, to maintain data integrity and avoid data loss.
- Benchmark Performance: Test the performance of FNV in your specific application to ensure it meets your speed requirements.
Conclusion: FNV’s Enduring Value in Hashing
The FNV hash function, with its simplicity, speed, and excellent distribution properties, continues to be a valuable tool in various computing domains. While not cryptographically secure, its efficiency and versatility make it an ideal choice for general-purpose hashing, especially when dealing with large datasets and performance-critical applications. Understanding the intricacies of FNV and its strengths and limitations allows developers to leverage its capabilities effectively, ensuring data integrity and optimizing application performance.




Closure
Thus, we hope this article has provided valuable insights into A Comprehensive Guide to the FNV Hash Function: Efficiency and Security in Hashing. We appreciate your attention to our article. See you in our next article!
You may also like
Recent Posts
- A Geographical Journey Through The Republic Of Congo: Unveiling A Nation’s Landscape And Potential
- Navigating Iowa’s Roads: A Comprehensive Guide To The Iowa DOT Road Condition Map
- Navigating Moreno Valley: A Comprehensive Guide To The City’s Layout
- The Power Of Maps: Understanding The Role Of Map Servers In The Digital Age
- Mastering The Battle Royale: The Importance Of Warm-Up Maps In Fortnite
- A Comprehensive Guide To Printable State Maps: Unveiling The Power Of Visualization
- The Missouri River: A Vital Lifeline Across The American Heartland
- Deciphering Nevada’s Political Landscape: A Guide To The Silver State’s Electoral Map
Leave a Reply